Main Content
Relax.
Security Professionals. Developers. Executives.
Our Mission
The Redpoint Security mission has always included helping security professionals and developers navigate the infosec world. As an application security firm, we have seen a range of clientele who manifest a whole host of differences.
Customer Journey
Redpoint's repeat customers tend to reduce number and risk-level of vulnerabilities during yearly or quarterly review, even with rapid rate of new feature development.
Assessments
Where does your organization need the most help?
SDLC in a waterfall process.
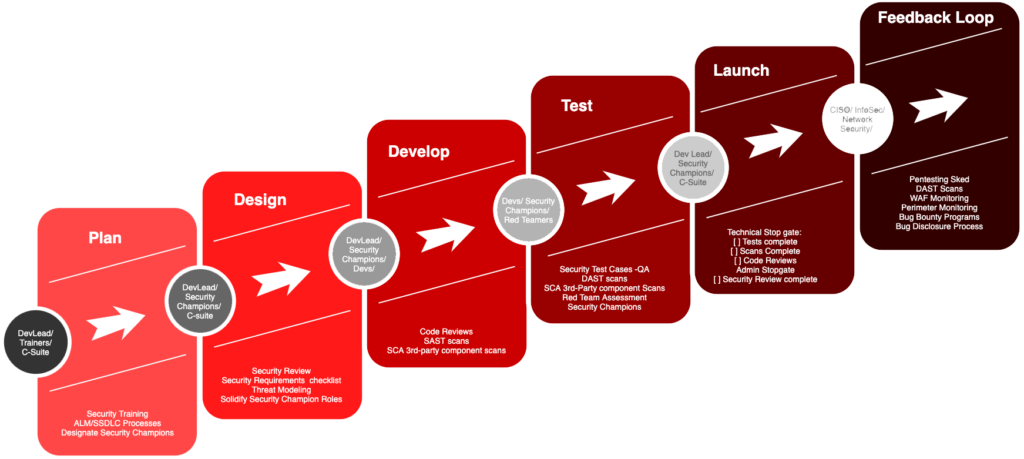
Our Story.
Founded in 2017, Redpoint Security is an application security consulting firm that is focused on all aspects of code security, whether through process improvement, framework research, or traditional application penetration testing. As speakers, contributors, and developers, our consultants have at least a decade of experience in the information security industry.
Work with Us (and relax).
The secret to comprehensive security is knowing how an attacker thinks and how a developer creates.
Code Security. By Coders.


